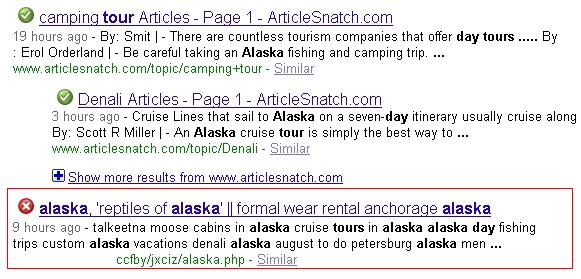
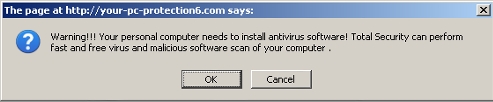
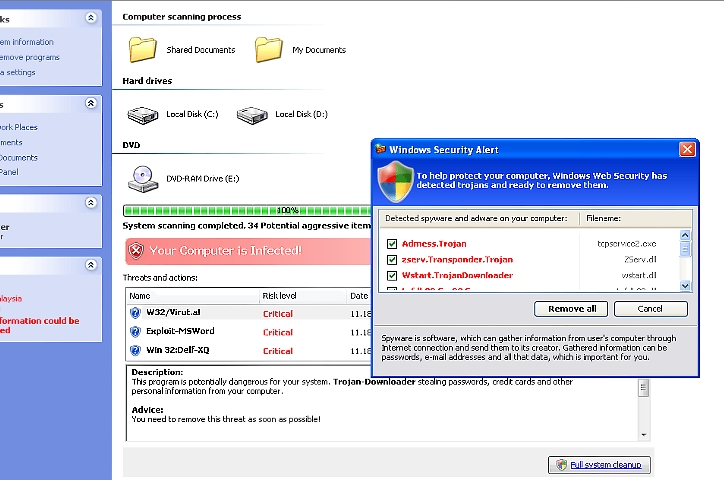
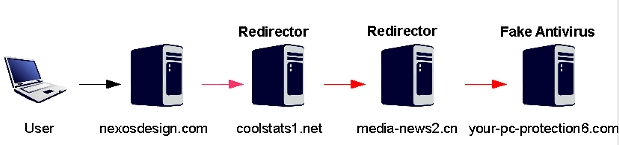
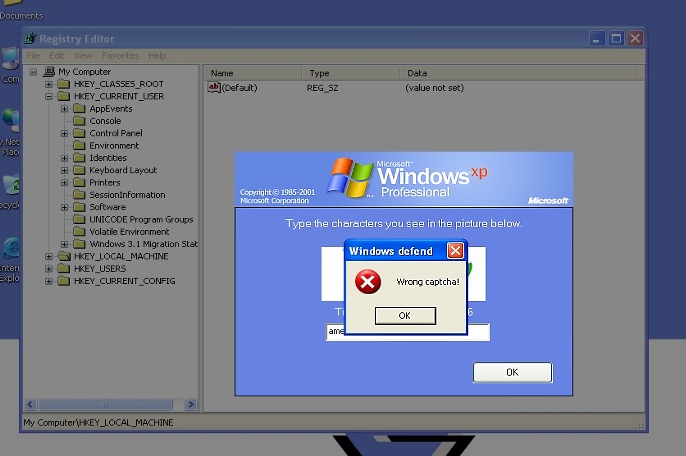
Another cybercriminal group is abusing the face of Facebook in another malware spam blast, fooling users to install banking password stealing malware and adware on their systems.
The message of the email claims to arrive from “The Facebook Team”, but in fact, the spam is spoofed and not from the team at all:
“Because of the measures taken to provide safety to our clients, your password has been changed.
You can find your new password in attached document.
Thanks,
The Facebook Team”
The real Facebook Team maintains threat-related information, “what-to-do-if” information, and security related stuff here.
The emails maintain an attachment that may have various names. Here are a some of the attachment names that when unzipped and run, ThreatFire has protected its community against in the past day:
Facebook_Password_e9081.zip
FACEBOOK_PASSWORD_52132.ZIP
Facebook_Password_6dd19.zip
Facebook_Password_4cf91.zip
FACEBOOK_PASSWORD_50573-1.ZIP
Facebook_Password_c92dd.zip
FACEBOOK_PASSWORD_7A343.zip

So what is being sent out? Unfortunately, the AV vendors that are starting to detect this variant do not always identify what they are detecting accurately (lucky that they are detecting it at all!). But in the end, the zipped attachment contains an armored downloader. Some of the spammed downloader executables drop multiple variants of multiple families. Adware, spyware, spambots, why not all of them? They are all money makers for this malware distribution group.
The malware package, in some cases, includes the highly active and highly malicious Zbot family. It seems that the Bredolab protector and dropper/downloader in active development has proven to be effective enough against AV scanner detections, so the crimeware groups are re-wrapping their zbot malware with it. Also interesting is that these two families of malware have recently been distributed by groups that implement methods to remove the other bot from victim systems. It’s been described as another “War of the Bots” with Bredolab v. Zbot. Clearly, this active cybercrime group is a separate one with different aims and no internal wars.

Koobface, Bredolab, and Zbot-distributing cybercrime groups all spoof Facebook and other highly popular social networking sites to deliver their malware to victim systems. Avoid the confusion and install a behavioral based layer of protection like ThreatFire that reliably and effectively prevents Bredolab, Zbot, and other highly dangerous malware families. Surf where you want, PC Tools Facebook group here.
The message of the email claims to arrive from “The Facebook Team”, but in fact, the spam is spoofed and not from the team at all:
“Because of the measures taken to provide safety to our clients, your password has been changed.
You can find your new password in attached document.
Thanks,
The Facebook Team”
The real Facebook Team maintains threat-related information, “what-to-do-if” information, and security related stuff here.
The emails maintain an attachment that may have various names. Here are a some of the attachment names that when unzipped and run, ThreatFire has protected its community against in the past day:
Facebook_Password_e9081.zip
FACEBOOK_PASSWORD_52132.ZIP
Facebook_Password_6dd19.zip
Facebook_Password_4cf91.zip
FACEBOOK_PASSWORD_50573-1.ZIP
Facebook_Password_c92dd.zip
FACEBOOK_PASSWORD_7A343.zip

So what is being sent out? Unfortunately, the AV vendors that are starting to detect this variant do not always identify what they are detecting accurately (lucky that they are detecting it at all!). But in the end, the zipped attachment contains an armored downloader. Some of the spammed downloader executables drop multiple variants of multiple families. Adware, spyware, spambots, why not all of them? They are all money makers for this malware distribution group.
The malware package, in some cases, includes the highly active and highly malicious Zbot family. It seems that the Bredolab protector and dropper/downloader in active development has proven to be effective enough against AV scanner detections, so the crimeware groups are re-wrapping their zbot malware with it. Also interesting is that these two families of malware have recently been distributed by groups that implement methods to remove the other bot from victim systems. It’s been described as another “War of the Bots” with Bredolab v. Zbot. Clearly, this active cybercrime group is a separate one with different aims and no internal wars.

Koobface, Bredolab, and Zbot-distributing cybercrime groups all spoof Facebook and other highly popular social networking sites to deliver their malware to victim systems. Avoid the confusion and install a behavioral based layer of protection like ThreatFire that reliably and effectively prevents Bredolab, Zbot, and other highly dangerous malware families. Surf where you want, PC Tools Facebook group here.