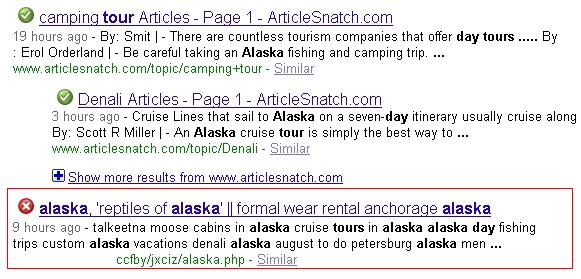
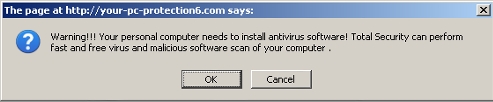
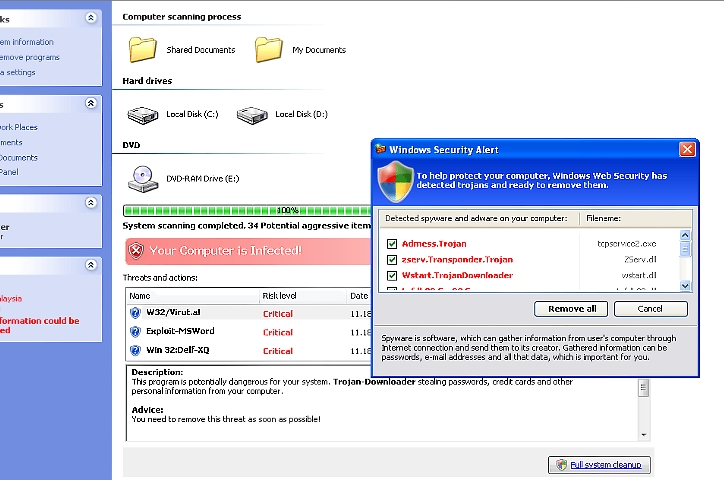
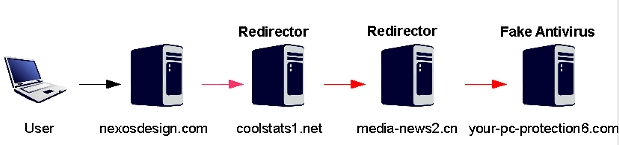
A fake
"conficker.b infection alert" spam campaign first observed in April, 2009 (using the following scareware domains
antivirus-av-ms-check .com;
antivirus-av-ms-checker .com;
ms-anti-vir-scan .com;
mega-antiviral-ms .com back then) is once again circulating in an attempt to trick users into installing "antispyware application", in this case the
Antivirus Pro 2010 scareware.
This campaign is directly related to
last week's Microsoft Outlook update campaign, with both of these using
identical download locations for the scareware.
The following is an extensive list of the domains involved in the campaigns:
abumaso3tkamid .com - Email: drawn@ml3.ru
afedodevascevo .com - Email: sixty@8081.ru
alertonabert .com - Email: flop@infotorrent.ru
alertonbgabert .com - Email: vale@e2mail.ru
alioneferkilo .com - Email: va@blogbuddy.ru
anobalukager .com - Email: chalkov@co5.ru
anobhalukager .com - Email: humps@infotorrent.ru
bufertongamoda .com - Email: kurt@8081.ru
buhafertadosag .com - Email: bias@co5.ru
buhervadonuska .com - Email: vale@e2mail.ru
bulakeskatorad .com - Email: bias@co5.ru
bulerkoseddasko .com - Email: bias@co5.ru
buleropihertan .com - Email: def@co5.ru
celiminerkariota .com - Email: morse@corporatemail.ru
certovalionas .com - Email: kurt@8081.ru
dabertugaburav .com - Email: def@co5.ru
elxolisdonave .com - Email: curb@cheapmail.ru
enkafuleskohuj .com - Email: kerry@freemailbox.ru
ertanueskayert .com - Email: xmas@co5.ru
ertonaferdogalo .com - Email: kerry@freemailbox.ru
ertu6nagertos .com - Email: recipe@isprovider.ru
ertubedewse .com - Email: weak@infotorrent.ru
ertugasedumil .com - Email: chalkov@co5.ru
ertugaskedumil .com - Email: humps@infotorrent.ru
ertunagertos .com - Email: def@co5.ru
erubamerkadolo .com - Email: kerry@freemailbox.ru
fedostalonkah .com - Email: bias@co5.ru
ftahulabedaso .com - Email: raced@corporatemail.ru
gumertagionader .com - Email: seize@e2mail.ru
huladopkaert .com - Email: chute@infotorrent.ru
iobacebauiler .com - Email: roy@corporatemail.ru
itorkalione .com - Email: pygmy@8081.ru
julionejurmon .com - Email: jacob@freemailbox.ru
julionermon .com - Email: pygmy@8081.ru
konitorsabure .com - Email: chalkov@co5.ru
konitorswabure .com - Email: humps@infotorrent.ru
lersolamaderg .com - Email: chalkov@co5.ru
lersolamgaderg .com - Email: humps@infotorrent.ru
linkertagubert .com - Email: kerry@freemailbox.ru
lionglenhrvoa .com - Email: sixty@8081.ru
liposdakoferda .com - Email: leaf@corporatemail.ru
lopastionertu .com - Email: cues@e2mail.ru
nebrafsofertu .com - Email: humps@infotorrent.ru
nuherfodaverta .com - Email: morse@corporatemail.ru
nulerotkabelast .com - Email: dealt@8081.ru
nulkersonatior .com - Email: dealt@8081.ru
obuleskinrodab .com - Email: xmas@co5.ru
ofaderhabewuit .com - Email: kerry@freemailbox.ru
okavanubares .com - Email: chalkov@co5.ru
okaveanubares .com - Email: humps@infotorrent.ru
onagerfadusak .com - Email: cues@e2mail.ru
orav4abustorabe .com - Email: drawn@ml3.ru
oscaviolaner .com - Email: larks@freemailbox.ru
ovuiobvipolak .com - Email: sixty@8081.ru
ovuioipolak .com - Email: bias@co5.ru
paferbasedos .com - Email: chalkov@co5.ru
pafersbasedos .com - Email: humps@infotorrent.ru
polanermogalios .com - Email: dealt@8081.ru
rdafergfvacex .com - Email: jacob@freemailbox.ru
rtugamer5tobes .com - Email: drawn@ml3.ru
rtugamertobes .com - Email: kw@co5.ru
scukonherproger .com - Email: kazoo@isprovider.ru
shuretrobaniso .com - Email: frail@infotorrent.ru
tarhujelafert .com - Email: raced@corporatemail.ru
tavakulio5nkab .com - Email: recipe@isprovider.ru
tavakulionkab .com - Email: def@co5.ru
tertunavogav .com - Email: la@freemailbox.ru
tertunwavogav .com - Email: drawn@ml3.ru
tsabunerkadosa .com - Email: humps@infotorrent.ru
 tsarbunerkadosa .com
tsarbunerkadosa .com - Email: humps@infotorrent.ru
tubanerdavaf .com - Email: chalkov@co5.ru
tubanerdavjaf .com - Email: halkov@co5.ru
uhajokalesko .com - Email: flop@infotorrent.ru
uhajokvfalesko .com - Email: flop@infotorrent.ru
ulioperdanogad .com - Email: vale@e2mail.ru
uliopewrdanogad .com - Email: kerry@freemailbox.ru
uplaserdunavats .com - Email: dealt@8081.ru
utka3merdosubor .com - Email: drawn@ml3.ru
utkamerdosubor .com - Email: kw@co5.ru
utorganedoskaw .com - Email: kerry@freemailbox.ru
utorgtanedoskaw .com - Email: xmas@co5.ru
uvgaderbotario .com - Email: def@co5.ru
vudermaguliermot .com - Email: leaf@corporatemail.ru
vuilerdomegase .com - Email: leaf@corporatemail.ru
vuilleskomandar .com - Email: seize@e2mail.ru
vulertagulermos .com - Email: dealt@8081.ru
vuretronulevka .com - Email: dealt@8081.ru
weragumasekasuke .com - Email: kazoo@isprovider.ru
werynaherdobas .com - Email: dealt@8081.ru
Despite the comprehensive portfolio of domains used, relying on spam to increase revenue from scareware sales is prone to fail, in this specific case due to the lack of event-based social engineering theme, something that was present in the first campaign.