Here's one fake Facebook site with a malicious JavaScript that uses the old "Flash Player upgrade installation" trick — but with a slight twist.
As usual, the viewer thinks they're going to see a video, if they just upgrade their Player:
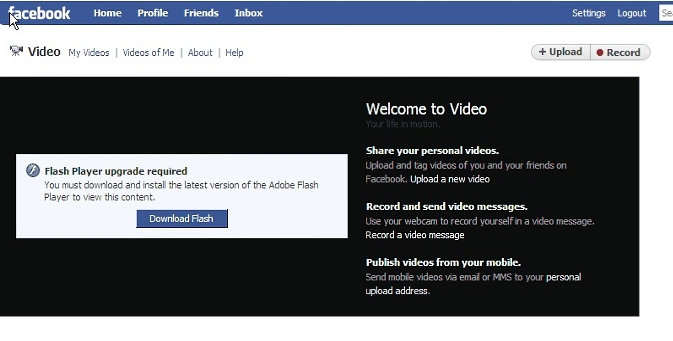
But first they have to download and install the "upgrade":

The unusual thing is, this "upgrade" comes with a CAPTCHA pop-up:

The request is displayed at random times and doesn't actually do anything. Anything entered into the field by the user results in this being displayed:
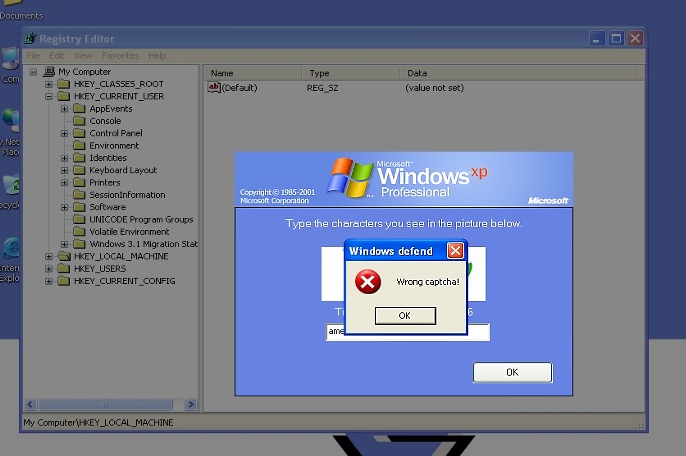
The screen will close after a few tries, but will still continue to appear off and on.
While the user is having dubious fun with the CAPTCHA test, the malware copies a couple files to C:\Windows, deletes itself, and creates a few Registry keys.

We detect the malware as Trojan:W32/Agent.MDN.
Our Browsing Protection blocks the whole fake Facebook website entirely. As usual though, be careful when you're surfing.
WebSecurity post by — Choon Hong




